Selam, Hello All,
While I was researching vulnerability on ZTE MF286R Mobile Modem on behalf of my customer, I have discovered a weaknesses on modem web management panel.
Here the details:
Product: ZTE MF286R Version: ZTE MF286R-1.0 (I have not tested other versions or modems)
Vulnerability Category: https://cwe.mitre.org/data/definitions/930.html
Broken Authantication and Session Management
An attacker can hijack the session of logged-in user by using brute-force method.
When I examined the “zwsd” cookie/session value, I thought that it is encrypted with MD5 function.
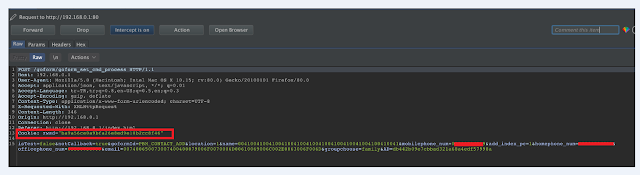 |
| ZTE MF286R-1.0 Modem Administrator zwsd Session Id is Using MD5 Weak Algorithm |
I have tried to crack it via wordlist and it was simply cracked.
The value “ba9a56ce0a9bfa26e8ed9e10b2cc8f46” was: 1876
 |
| zwsd Value Has Been Cracked with a successful dictionary brute-force attack |
After re-logged-in the application, it has created a new weak digit numbers by encrypting md5 function like md5(11834) , md5(11506) etc…
So when I see the results, I have decided that it was easy to hijack a user session. Because when a user logged-in to the web management panel, I can brute session value by using burp-suite proxy tool easily.
Here the burp suite intruder module settings:
 |
| Burp Suite Settings For Attacking Administrator Login |
A few seconds later, it has succesfully hijacked the user session value md5(4738) namely c2e06e9a80370952f6ec5463c77cbace
So I can define this cookie value in the browser and succesfully logged-in application, or send malwormed requests to modem web application.
 |
| Administrator Session Hijacked |
Since I could not get response to the email I sent to ZTE Corp on 10 October 2020 , I decided to share it.
Regards
Emrullah Akdemir
CEO - TRYSEC Corp.
Hiç yorum yok:
Yorum Gönder